SAML Authentication
SAML Authentication is only available on 'On-Premise' Offers
If you coordinate your companies authentication over a SAML provider such as Okta or Google GSuite SAML, you can easily integrate and start using right away. The following documentation is organized for integrating Google GSuite SAML App. However, the same principles apply for any SAML2 provider such as Okta.
Check that your rakam-bi container has the following environment variables available;
| Variable | Example Value | Description |
|---|---|---|
| RAKAM_CONFIG_SITE__URL | https://your-rakam-bi-url.com | Should point to your load balancers A/CNAME. You may verify this using the shell command: dig A your-rakam-bi-url.com @8.8.8.8 |
| RAKAM_CONFIG_SAML_COOKIE__DURATION* | 5h (the default value) | Time to live of a cookie acquired via SAML login. |
- Optional variable
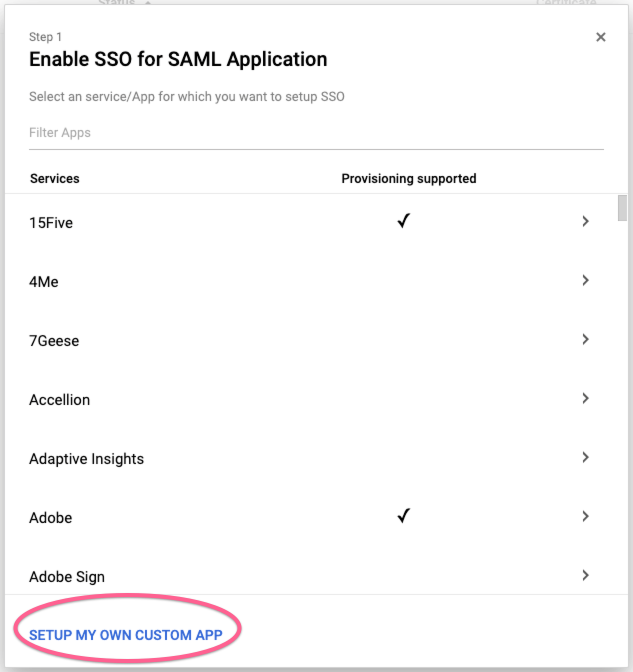
1. Create a new SAML App
Navigate to your SAML Apps at your GSuite admin console. Select 'SETUP MY OWN CUSTOM APP'
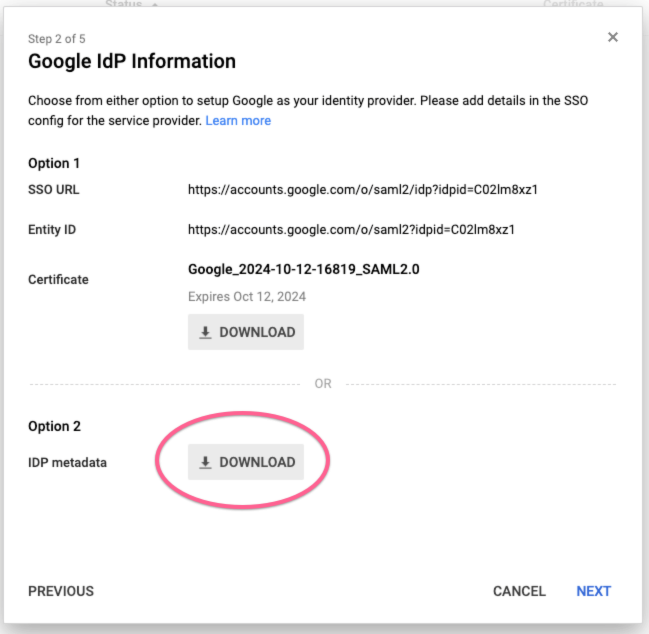
2. Download IDP Metadata
Click on 'Download' button and save the XML file.
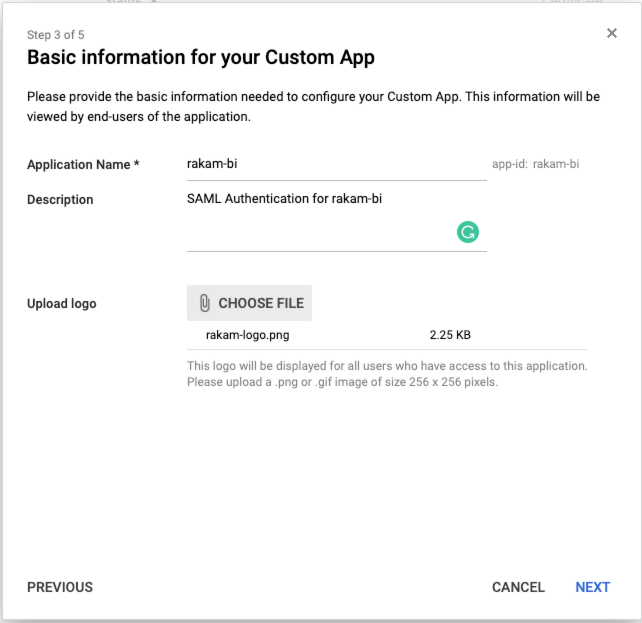
3. Name your application
You can choose any name for this SAML App, description and logo are optional.
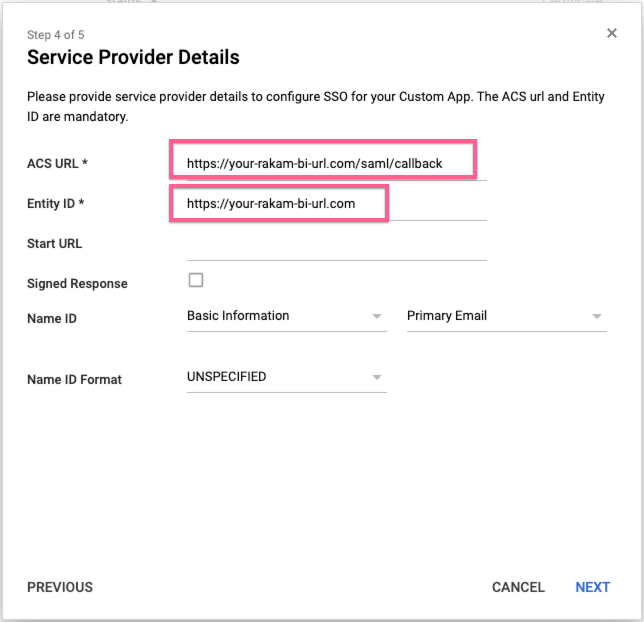
4. Enter Service Provider Details
Enter the following URL's of your Rakam-BI deployment.
- ACS URL:
https://your-rakam-bi-url.com/saml/callback - Entity ID:
https://your-rakam-bi-url.com
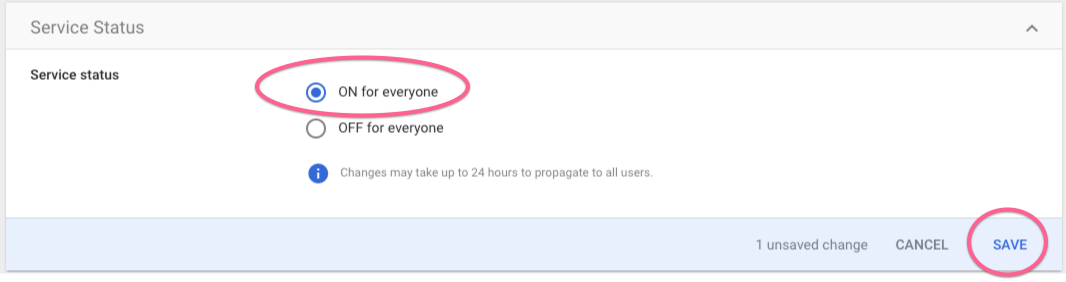
5. Activate the App for your users
Click to 'Edit Service' and under 'Service Status' section toggle ON for everyone
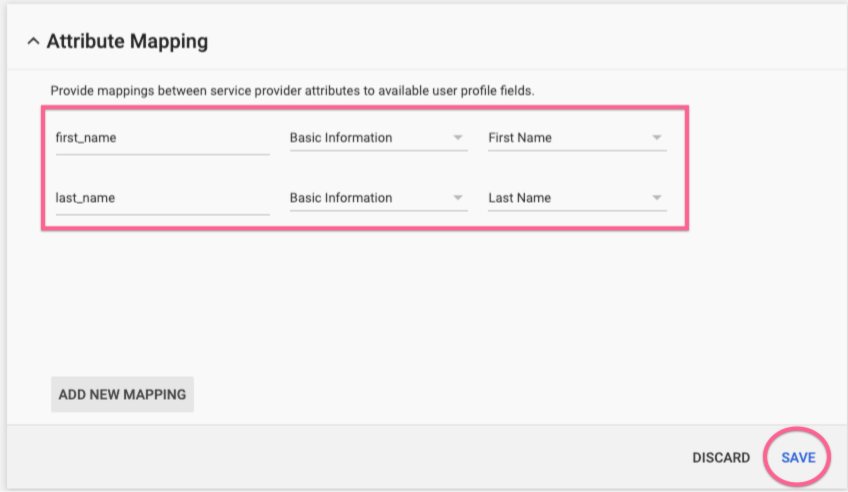
6. Mapping First and Last Names (Optional)
If you which to map your user's first and last names to rakam-bi, navigate to 'Attribute Mapping' and map the following fields. By default, users with SAML authentication are not able to create projects. If you choose to disable this, you can add a static mapping from rakam_group to rakam_supervisor
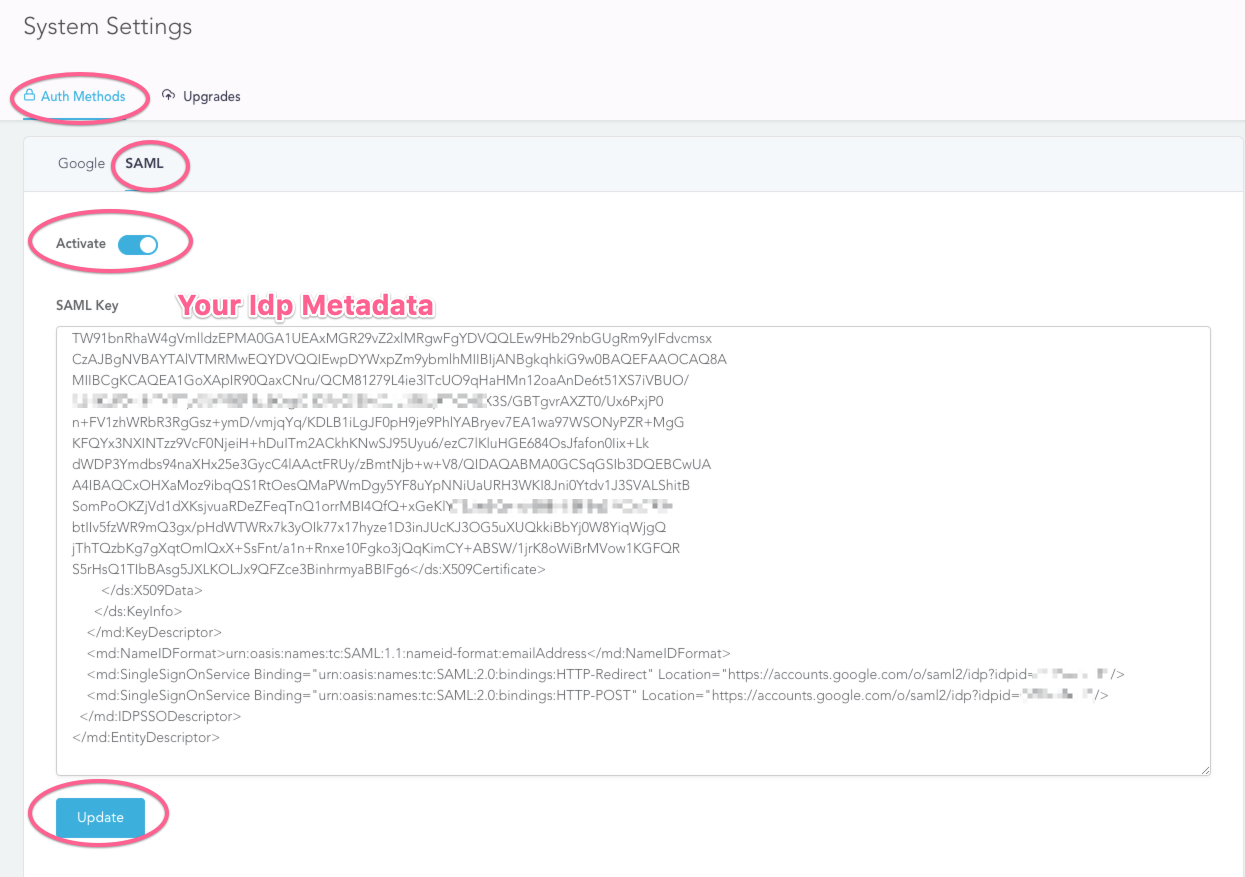
7. Update SAML Idp Metadata on Rakam-BI Admin Page
Log in with your administrator account (the first account you registered to your rakam-bi deployment.) .Navigate to your administration page on rakam-bi (htttps://your-rakam-bi-url.com/admin/auth). Select the SAML section and paste your Idp metadata XML contents.
You can verify the installation via logging out and locating 'Connect via SAML' button. Once this integration enabled, registration of local accounts is not possible. Although already registered users will be able to log in over 'Use a Local User' option.
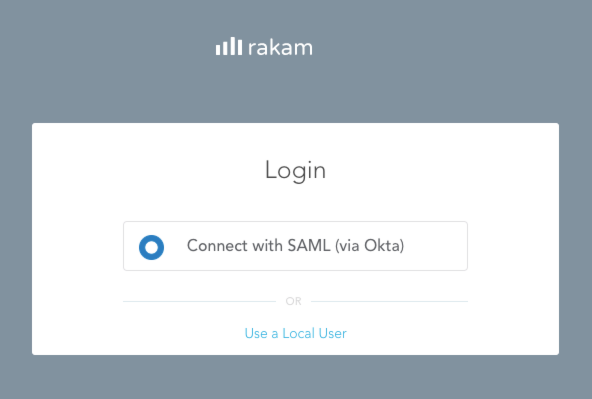
Once a local user is logged in using SAML, it is not possible to log in using local credentials anymore but the administrator user
Updated over 6 years ago